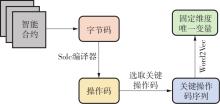
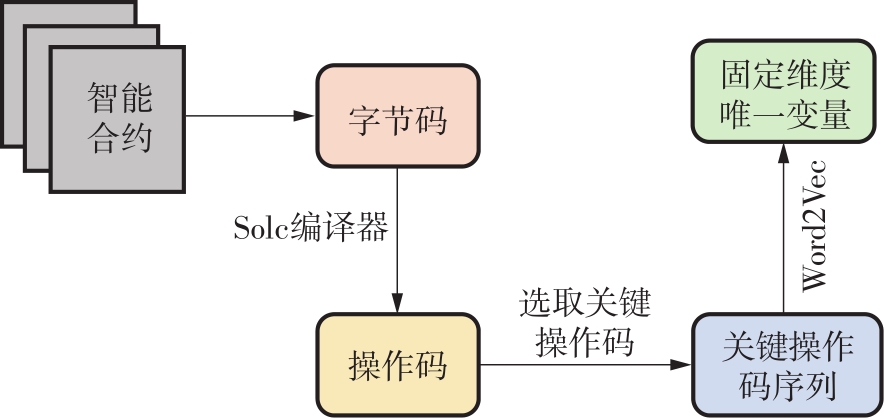
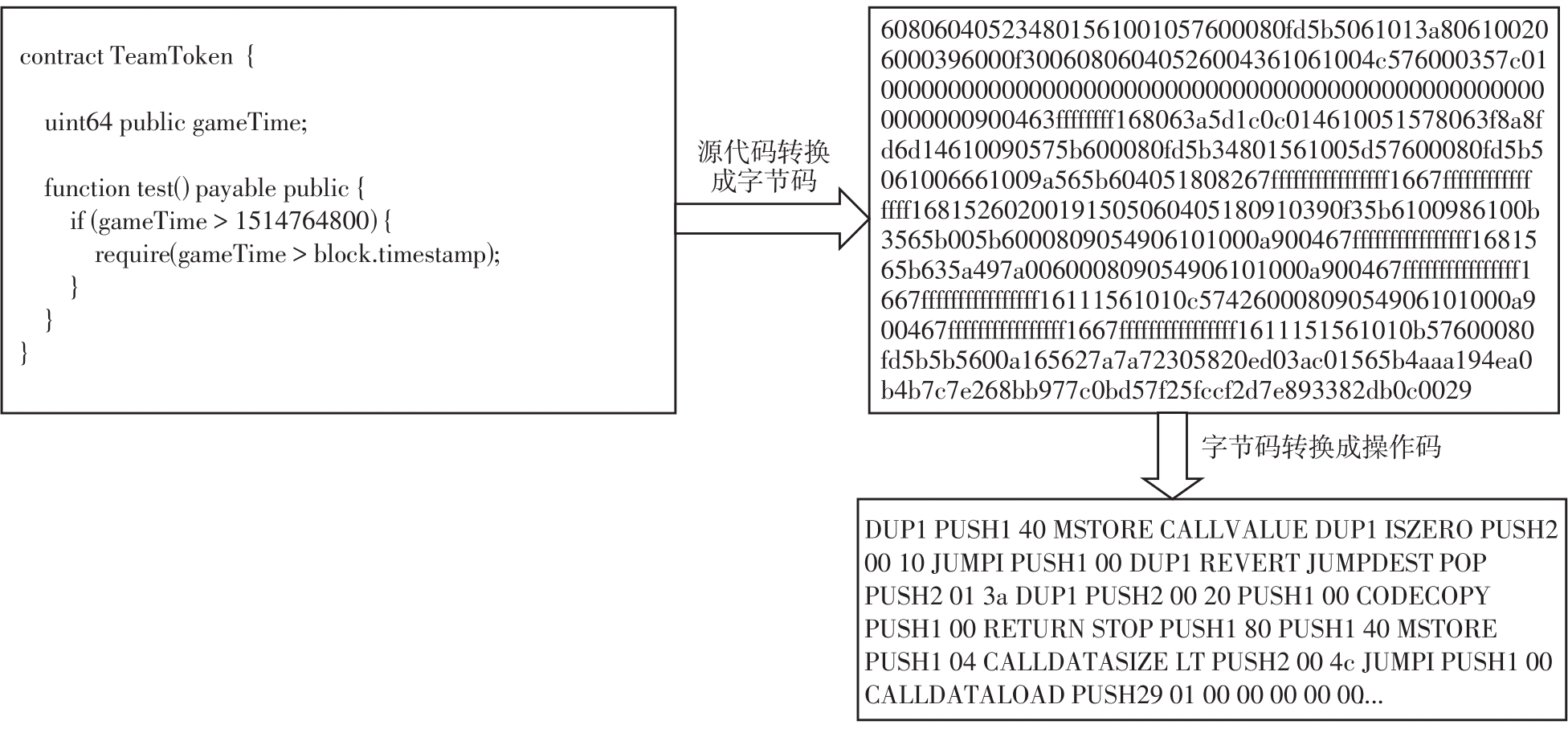
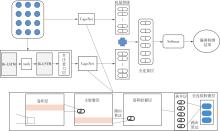
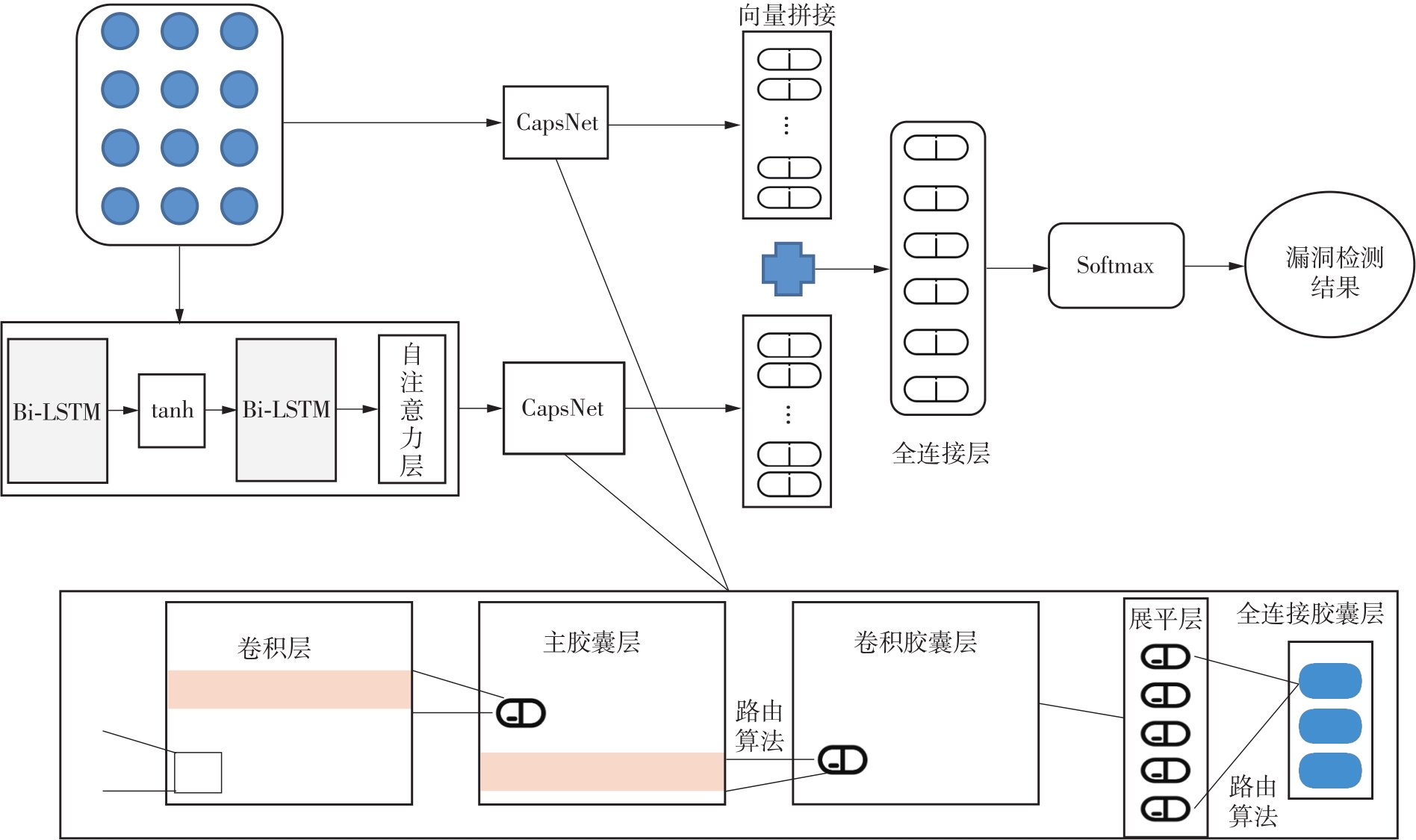
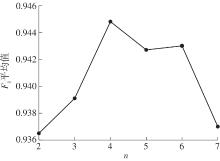
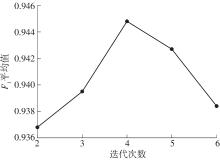
| 1 |
DHILLON V, METCALF D, HOOPER M .The DAO hacked[M]∥ Blockchain enabled applications.Berkeley:Apress,2017:67-78.
|
| 2 |
DANNEN C .Introducing Ethereum and solidity[M].Berkeley:Apress,2017:69-88.
|
| 3 |
LUU L, CHU D H, OLICKEL H,et al .Making smart contracts smarter[C]∥ Proceedings of the 2016 ACM SIGSAC Conference on Computer and Communications Security.Vienna:ACM,2016:254-269.
|
| 4 |
JIANG B, LIU Y, CHAN W K .ContractFuzzer:fuzzing smart contracts for vulnerability detection[C]∥ Proceedings of 2018 the 33rd IEEE/ACM International Conference on Automated Software Engineering.Montpellier:IEEE,2018:259-269.
|
| 5 |
KALRA S, GOEL S, DHAWAN M,et al .ZEUS:analyzing safety of smart contracts[C]∥ Proceedings of 2018 Network and Distributed Systems Security Symposium.San Diego:Internet Society,2018:1-12.
|
| 6 |
LATTNER C, ADVE V .LLVM:A compilation framework for lifelong program analysis and transformation[C]∥ Proceedings of 2004 International Symposium on Code Generation and Optimization.San Jose:IEEE,2004:1-12.
|
| 7 |
GURFINKEL A, KAHSAI T, NAVAS J A .SeaHorn:a framework for verifying C programs (competition contribution)[C]∥ Proceedings of the 21st International Conference on Tools and Algorithms for the Construction and Analysis of Systems.London:Springer,2015:447-450.
|
| 8 |
ZHUANG Y, LIU Z, QIAN P,et al .Smart contract vulnerability detection using graph neural network[C]∥ Proceedings of the Twenty-Ninth International Joint Conference on Artificial Intelligence.Yokohama:International Joint Conferences on Artificial Intelligence,2020:3283-3290.
|
| 9 |
LIU Z, QIAN P, WANG X,et al .Combining graph neural networks with expert knowledge for smart contract vulnera bility detection[J].IEEE Transactions on Knowledge & Data Engineering,2021,35(2):1296-1310.
|
| 10 |
沈晨凯 .基于深度学习的智能合约漏洞检测方法研究[D].武汉:武汉大学,2021.
|
| 11 |
WANG W, SONG J, XU G,et al .ContractWard:automated vulnerability detection models for Ethereum smart contracts[J].IEEE Transactions on Network Science and Engineering,2020,8(2):1133-1144.
|
| 12 |
TANN W J W, HAN X J, GUPTA S S,et al .Towards safer smart contracts:a sequence learning approach to detecting security threats[EB/OL]. (2018-11-16)[2022-03-30]..
|
| 13 |
SABOUR S, FROSST N, HINTON G E .Dynamic routing between capsules[C]∥ Proceedings of the 31st International Conference on Neural Information Processing Systems.Long Beach:ACM,2017:3859-3869.
|
| 14 |
SHAW P, USZKOREIT J, VASWANI A .Self-attention with relative position representations[C]∥ Proceedings of 2018 Conference of the North American Chapter of the Association for Computational Linguistics:Human Language Technologies.New Orleans:Association for Computational Linguistics,2018:464-468.
|
| 15 |
ZHAO W, YE J, YANG M,et al .Investigating capsule networks with dynamic routing for text classification[C]∥ Proceedings of 2018 Conference on Empirical Methods in Natural Language Processing.Brussels:Association for Computational Linguistics,2018:3110-3119.
|
| 16 |
DURIEUX T, FERREIRA J F, ABREU R,et al .Empirical review of automated analysis tools on 47587 Ethereum smart contracts[C]∥ Proceedings of the 42nd International Conference on Software Engineering.Seoul:Association for Computing Machinery,2020:530-541.
|
| 17 |
CHEN J, XIA X,LO D,et al .Defining smart contract defects on Ethereum[J].IEEE Transactions on Software Engineering,2022,48(1):327-345.
|
| 18 |
MUELLER B .Mythril:a reversing and bug hunting framework for the Ethereum blockchain[EB/OL].(2017-11-08)[2022-03-30]..
|
| 19 |
TIKHOMIROV S, VOSKRESENSKAYA E, IVANITSKIY I,et al .SmartCheck:static analysis of Ethereum smart contracts[C]∥ Proceedings of 2018 IEEE/ACM the 1st International Workshop on Emerging Trends in Software Engineering for Blockchain.Gothenburg:IEEE,2018:9-16.
|
| 20 |
TSANKOV P, DAN A, DRACHSLER-COHEN D,et al .Securify:practical security analysis of smart contracts[C]∥ Proceedings of 2018 ACM SIGSAC Conference on Computer and Communications Security.Toronto:ACM,2018:67-82.
|
| 21 |
GAO Z, JAYASUNDARA V, JIANG L,et al .SmartEmbed:a tool for clone and bug detection in smart contracts through structural code embedding[C]∥ Proceedings of 2019 IEEE International Conference on Software Maintenance and Evolution.Cleveland:IEEE,2019:394-397.
|
| 22 |
GOGINENI A K, SWAYAMJYOTI S, SAHOO D,et al .Multi-class classification of vulnerabilities in smart contracts using AWD-LSTM,with pre-trained encoder inspired from natural language processing[J].IOP SciNotes,2020,1(3):035002/1-6.
|